
Les pirates de l’indexation
À l’époque, non plus de l’internet, mais de la vulgarisation des techniques de Web marketing, la course aux résultats est devenue une priorité universelle. Les canaux traditionnels de ventes sont bouleversés par l’arrivée des ‘nouveaux modes de consommation’ des internautes, qui se ruent en grand nombre sur des nouveaux services qui n’existaient pas quelques mois auparavant.
Proportionnellement au nombre des entrepreneurs en quête d’une plus grosse part du gâteau, les pratiques habituelles laissent la place à des méthodes plus sombres, aux résultats redoutablement efficace. Ces spécialistes du Web connaissent, chacun à leur manière, les bonnes pratiques, les faiblesses et les raccourcis permettant d’augmenter leur revenus.
Qui en fait donc usage ?

- Le « White hat » SEO – chevalier vertueux des temps modernes, bâtissant une autorité naturelle et saine autours d’un contenu pensé pour l’usager. Ce genre de pratiques respecte complètement les consignes de qualité de Google.
- Le « Black hat » SEO – chevalier noir de l’internet, utilise toutes les techniques sombres que proposent l’internet pour, non seulement créer et générer du contenu, mais également bâtir une autorité à partir de raccourcis, de « hacks », et d’autres manipulation spécifiques.
- Le « Grey hat » SEO – mélange subtil entre le white hat, discipliné et respectueux, et le « Black hat », cherche à suivre les lignes directrices de Google tout en utilisant d’autres techniques plus ‘sombres’ et moins risquée pour parvenir à augmenter ses rankings dans les engins de recherche.
 Le Black Hat SEO
Le Black Hat SEO
Les experts de ce type de référencement proviennent des milieux proches de l’éducation des cybercriminels, ou cyberterroristes, qui utilisent consciemment leur connaissance dans le but de détruire, nuire, ou voler des informations. Leur nombre est amené à s’agrandir dans les prochaines années avec la valeur grimpante liées aux informations d’espionnage industriel dans un contexte de guerre économique. En matière de référencement pur, les méthodes liées à l’extraction de l’information récupérée par les crawlers (ou robots d’exploration des engins de recherche) sont utilisées.
Google Dorking :
Le Google Dorking est un terme qui se réfère à la pratique de l’application des techniques de recherche de pointe grâce aux paramètres du moteur de recherche. Son but est de découvrir des informations confidentielles des entreprises et des individus qui ne serait généralement pas sortis à la suite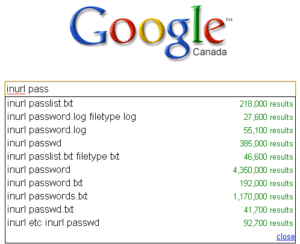 d’une recherche ‘normale’.
d’une recherche ‘normale’.
Les Black Hat peuvent utiliser des tactiques Google Dorking pour révéler des informations que les entreprises et les individus. Ces informations peuvent inclure, pour les SEO : des listes de liens entrants, les partenariats, l’ensemble des backlinks, les plateformes sur lesquelles il est possible de commenter, etc….
Pour les pirates, ces informations peut aller jusqu’aux : noms d’utilisateur et mots de passe de compte , listes et des détails des clients et partenaires , des documents sensibles et privés , des vulnérabilités pour les cyber-attaques potentielles et plus encore.
L’utilisation de Scripts
Une fois l’information récoltée, le temps passe à son exploitation. Ce qui différencie certainement à coup sur, les Black Hat SEO des autres, est l’utilisation de softwares, ou de scripts, permettant, non seulement de lancer des ‘dorks’ en masse, mais d’exploiter les résultats trouvés. De nombreux logiciels existent afin de poster en masse sur différentes plateformes, qu’il s’agisse d’articles, de blogs, de Bookmarks, de commentaires ou de profils.
Dans ses consignes, Google nous mets en garde à propos de la mise en place « des systèmes de liens qui peuvent avoir un impact négatif sur le classement d’un site dans les résultats de recherche ».
Parmi ces « systèmes de liens », Google s’en prend à l »utilisation de programmes ou services automatisés pour créer des liens entrants, étant donné le nombre d’outils permettant de générer ces précieux liens retours.
Il existe en effet de nombreux outils utilisés par des Black Hat SEO permettant de générer automatiquement, et massivement, de précieux backlinks tel que SenukeX, Xrummer, SlickSubmitter, et plusieurs autres.

Les redirections trompeuses
Google informe que « certaines redirections ont pour but de tromper les moteurs de recherche ou de présenter un contenu différent aux internautes et aux moteurs de recherche. » Il est évident que de telles redirections sont parfois utilisées dans le but de favoriser des rankings, ce qui est largement interdit par Google.
Le cloaking
Le cloaking » consiste à présenter aux visiteurs réels un contenu différent de celui destiné aux moteurs de recherche.
Cette technique de dissimulation constitue depuis longtemps une pénalité google pour ceux qui l’emploient. Exemple officiellement condamné de cloaking : du texte ou des mots clés sont affichés sur la page , et dans le code, seulement si le user-agent qui requête la page correspond à un robot d’exploration et de recherche, et non à un internaute.
 Negative SEO
Negative SEO
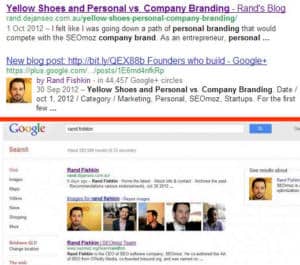
Vous vous en doutez : si il est possible de monter un site dans les résultats des engins de recherche, il est alors possible de le descendre. Le negative SEO part du principe de l’application des pénalités. Le fait de duppliquer, par exemple, un site existant, a pour effet potentiel la baisse de l’article original dans les résultats de recherche. Dan Petrovic à réussi, en reprenant le code d’une page liée à Rand Fishkin, à dépasser la page originale sur le mot clé : » Rand Fishkin ». Belle preuve !
De la même manière, il est possible de soumettre un site à plusieurs liens ou backlinks de mauvaise qualité, ou aux ancrages ‘impertinents’. L’effet sera à terme celui d’une pénalisation automatique ou manuelle de la part de Google.
Des questions ?
